This article describes the node deploy configuration file. It provides an overview of how node deploy configuration files are used, a conceptual model of the node deploy configuration file, and a detailed description of all configuration values.
This chapter assumes that you are familiar with the configuration file syntax described in HOCON Syntax Reference.
The node deploy configuration file is used to define deployment-time values, and to also override, and possibly augment, default application configuration. Deployment time configuration can be specified for multiple nodes in a single node deploy configuration file. The nodes can be in the same or different clusters. The node configuration to use from the node deploy configuration file when installing a node is determined by matching the node name being installed with a node name in the node deploy configuration file. This is shown in Example 1, “Node configuration selection”.
Example 1. Node configuration selection
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy
{
//
// Define a cluster X with three nodes
//
nodes =
{
//
// Node A.X configuration
//
"A.X" = { }
//
// Node B.X configuration
//
"B.X" = { }
//
// Node C.X configuration
//
"C.X" = { }
}
}
}
//
// Install node A.x - use A.X node configuration in nodedeploy.conf
//
epadmin install node --nodename=A.X ... --nodedeploy=nodedeploy.confNode deployment configuration files can be specified on the install node command line, or they can be packaged in an application archive. Packing a node deployment configuration in an application archive provides an easy mechanism to ship application specific default node deploy configuration values.
In addition to the configuration data defined in a node deploy configuration file, the node deploy configuration can also contain arbitrary configuration. There are two sections in the node deploy configuration file for this configuration:
-
global — applies to all nodes defined in the node deployment configuration file. See NodeDeploy for details.
-
per-node — applies to a specific node in the node deployment configuration file. See Node for details.
Warning
Configuration embedded in the global and per-node sections
of a node deployment configuration file are only processed when
the node deployment configuration file is passed to
install node. Any
configuration in these sections is ignored when loading and
activating configuration using the load and
activate configuration
commands.
Configuration files can also be contained in the fragments in an application archive and in the application itself.
See 2 for details on configuration load order.
The node deploy configuration is audited whenever it changes state, such as load to active. There are detailed audits for each of the configuration objects in the node deploy configuration file. These are described in Configuration Objects. There are also these audits enforced on node deploy configuration during application installation.
-
Node deploy configuration can only be contained in an application archive. Node deploy configurations cannot be contained in fragment archives. Node deploy configurations found in a fragment archive will cause an audit failure during application installation.
-
There can only be a single node deploy configuration in an application archive. Multiple node deploy configurations in an application archive will cause an audit failure during application installation.
-
All node deploy configurations loaded when a node is installed must have the same configuration name. Node deploy configurations with different configuration names will cause an audit failure during application installation.
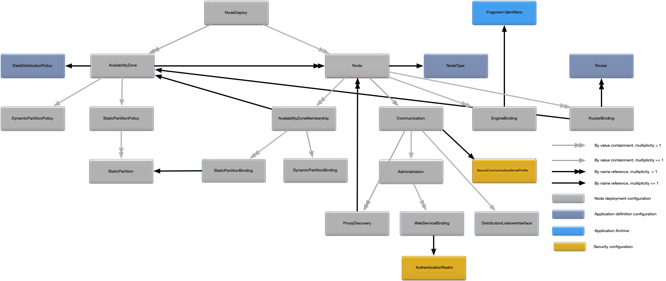
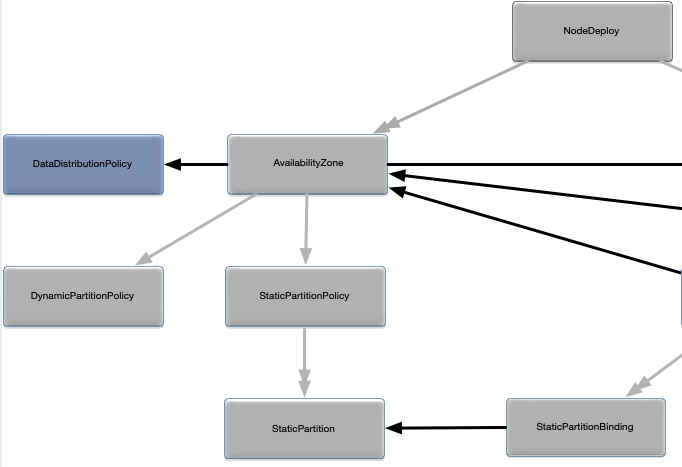
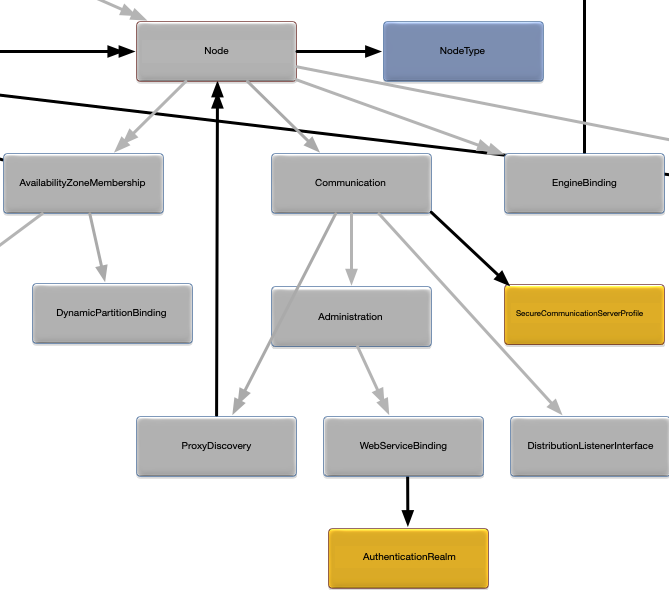
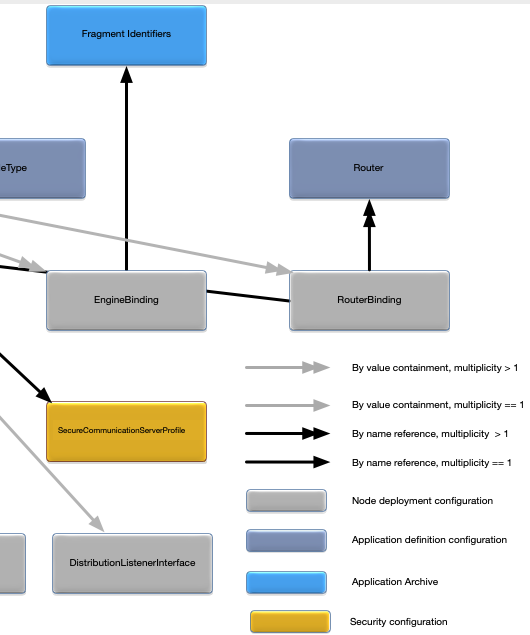
Figure 1, “Node deployment configuration map” shows a map of the relationships between all of the configuration objects in a node deployment configuration file. It also shows all external relationships to the application definition configuration and the application archive.
See the following slices of this map, blown up to readable size. First, the left side:
 |
The center:
 |
And the right side:
 |
The node deploy configuration has a configuration type of
com.tibco.ep.dtm.configuration.node.
This section provides detailed descriptions for all properties in each node deploy configuration object. A snippet is also provided for each configuration object showing the syntax for specifying all of the configuration values.
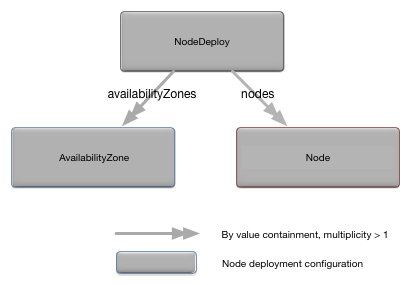
The NodeDeploy object is the top-level
container for all of the node deploy configuration. Figure 2, “NodeDeploy relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in NodeDeploy object properties and a snippet for these properties is in Example 2, “NodeDeploy object snippet”.
NodeDeploy object properties
| Name | Type | Description |
|---|---|---|
|
Associative array of Node objects
keyed by fully qualified node service name.
|
Nodes (see Node) configured in this file. The nodes may be in the same or different clusters. At least one node must be defined. |
|
Associative array of AvailabilityZone
objects keyed by availability zone name.
|
Availability zone configurations (see AvailabilityZone). Optional. No default. |
globalConfiguration |
String [ ] | Array of configuration data that applies to all configured nodes. Optional. No default. |
Example 2. NodeDeploy object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
globalConfiguration =
[
"""
name = "mysecurity"
type = "com.acme.security.keystore"
version = "1.0.0"
configuration =
{
CommunicationSecurity =
{
keyStore = "myKeyStore.jks"
keyStorePassword = "secret"
}
}
"""
]
nodes =
{
"A.X" = { ... }
"B.X" = { ... }
"C.X" = { ... }
}
availabilityZones =
{
"elastic-credit" = { ... }
"elastic-debit" = { ... }
}
}
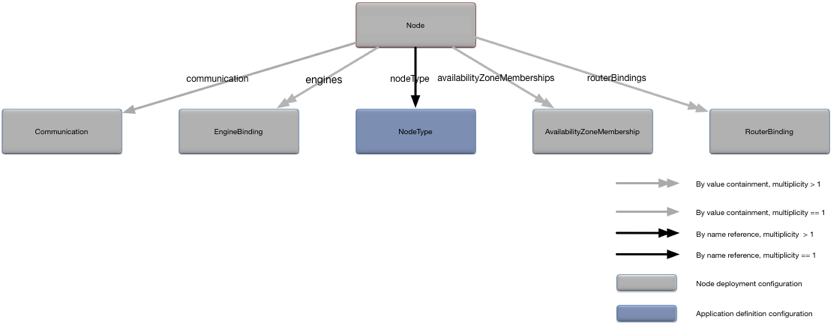
}The Node object defines the
configuration for a specific node. Figure 3, “Node relationships” shows the relationships to other
configuration objects.
A detailed description of the configuration object properties is in Node object properties and a snippet for these properties is in Example 3, “Node object snippet”.
Node object properties
| Name | Type | Description |
|---|---|---|
|
String | The node's type, as defined in the application definition
configuration. Optional. Default value is a built-in node type
of default.
|
|
String | Node description. Optional. Default value is node name. |
|
Associative array of EngineBinding
objects keyed by engine name.
|
Engine bindings (see EngineBinding) for this node. Optional. Default runs a single engine for each top-level fragment in the node type being deployed on the node. |
|
Communication configuration
object.
|
Network communication configuration for the node. Optional. See Communication for default values. |
|
String [ ] | Array of configuration data that applies to this node. Optional. No default. |
|
Associative array of
AvailabilityZoneMembership objects keyed by
availability zone names.
|
Availability zone membership for the node (see AvailabilityZoneMembership). The
availability zone must be defined in
NodeDeploy.availabilityZones. Optional. No
default.
|
|
RouterBinding [ ]
|
Router bindings for the node (see RouterBinding). Optional. No default. |
Example 3. Node object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
nodeType = "large-resources"
description = "My application node"
engines =
{
"settlement-engine" = { ... }
}
communication = { ... }
configuration =
[
"""
name = "mysecurity"
type = "com.acme.security.keystore"
version = "1.0.0"
configuration =
{
CommunicationSecurity =
{
keyStore = "myKeyStore.jks"
keyStorePassword = "secret"
}
}
""",
"""
name = "myusers"
type = "com.acme.security.users"
version = "1.0.0"
configuration =
{
Principal =
{
principal = "road-runner"
}
}
"""
]
availabilityZoneMemberships =
{
"cross-data-center" = { ... }
}
routerBinding =
[
{ ... }
]
}
}
}
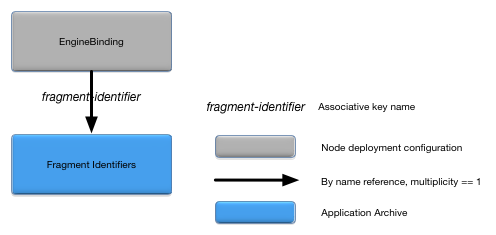
}The EngineBinding object associates an
engine name with it's fragment and optional engine specific
configuration. Figure 4, “EngineBinding relationships” shows
the relationships to other configuration objects.
A detailed description of the configuration object properties is in EngineBinding object properties and a snippet for these properties is in Example 4, “EngineBinding object snippet”.
Example 4. EngineBinding object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
engines =
{
"settlement-engine" =
{
fragmentIdentifier = "settlement-engine-fragment"
configuration =
[
"""
name = "my-engine-stuff"
type = "com.acme.engine"
version = "1.0.0"
configuration =
{
AcmeEngine =
{
name = "value"
}
}
"""
]
}
}
}
}
}
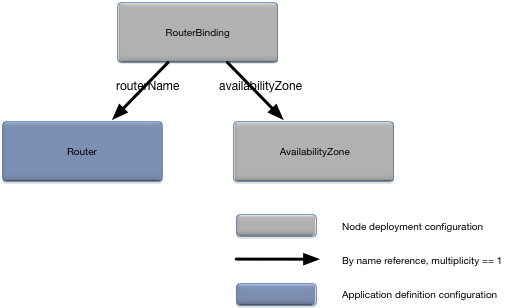
}The RouterBinding object associates a
router with a node and optionally an availability zone. Figure 5, “RouterBinding relationships” shows the relationships to
other configuration objects.
A detailed description of the configuration object properties is in RouterBinding object properties and a snippet for these properties is in Example 5, “RouterBinding object snippet”.
RouterBinding object properties
| Name | Type | Description |
|---|---|---|
|
String | Router to associate with this node. A router with this name must exist in the application definition configuration. Required. |
|
Reference to AvailabilityZone
object.
|
Associate a router with an availability zone (see AvailabilityZone). If specified, the availability zone must exist in the node deploy configuration file. Optional. Router is not associated with an availability zone by default. |
Example 5. RouterBinding object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
routerBindings =
[
{
routerName = "my-partition-router"
availabilityZone = "active-active"
}
{
routerName = "my-round-robin-router"
}
]
}
}
}
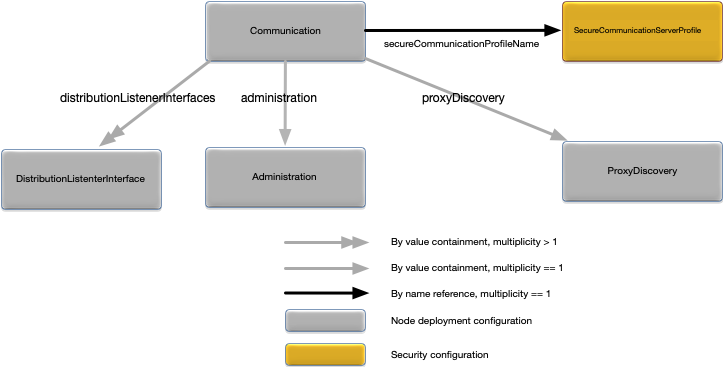
}The Communication object defines all
connectivity options for a node. Figure 6, “Communication relationships” shows the relationships
to other configuration objects.
A detailed description of the configuration object properties is in Communication object properties and a snippet for these properties is in Example 6, “Communication object snippet”.
Communication object properties
| Name | Type | Description |
|---|---|---|
|
Administration configuration
object.
|
Administration network communication configuration for the node. Optional. See Administration for the default values. |
|
long | Broadcast discovery port. Optional. Default value is
54321.
|
|
String [ ] | An array of broadcast discovery network request
addresses. The addresses are specified as either IPV4 or DNS
host names. Discovery requests are broadcast to the
discoveryPort on the network interface
associated with each network address. Optional. Default value is
a single network address which is the system host name.
|
|
DistributionListenerInterface [ ] of
configuration objects.
|
Distribution network communication configuration for the node. Optional. See DistributionListenerInterface for the default values. |
|
long | The number of ports to allocate to the node for
distribution listeners. Ports are allocated from this range when
migrating the distribution listener between engines or when a
duplicate port error is detected starting a listener. Port
allocation is started at the configured
dataTransportPort for each distribution
listener interface (see DistributionListenerInterface). The minimum
value that can be specified is the total number of engines plus
one. If a port cannot be allocated from this range, the
distribution listener will fail to start. Optional. Default
value is 20.
|
|
ProxyDiscovery configuration
object.
|
Proxy discovery configuration for the node (see ProxyDiscovery). Optional. No default. |
|
String | Name of a secure communication server profile (see Runtime Security Configuration) to use to configure secure communications for the node's administration, data transport, and web server listeners. The secure communication server profile must include a truststore. The truststore is used to validate certificates sent from other nodes in the cluster. Optional. No default. |
Example 6. Communication object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
numberSearchPorts = 10
discoveryPort = 4321
discoveryRequestAddresses = ["myhost.com"]
distributionListenerInterfaces = [ ... ]
administration = { ... }
proxyDiscovery = { ... }
secureCommunicationProfileName = "my-secure-communication-server-profile-name"
}
}
}
}
}The DistributionListenerInterface
object defines the network communication options for a node's
distribution connectivity. Figure 7, “DistributionListenerInterface relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in DistributionListenerInterface object properties and a snippet for these properties is in Example 7, “DistributionListenerInterface object snippet”.
Warning
IP addresses specified in the address
configuration property must be quoted. See Example 7, “DistributionListenerInterface object snippet”.
DistributionListenerInterface object properties
| Name | Type | Description |
|---|---|---|
|
long | Distribution listener port number. This field is required
and cannot have a value of 0 if the Node
configuration (see Node) containing the
DistributionListenerInterface object is
referenced in ProxyDiscovery configuration
(see ProxyDiscovery),
otherwise optional. Default value is 0, which
causes the distribution port to be auto-assigned when the node
is installed.
|
|
boolean | Deprecated secure-transport indicator. Use the
secureCommunicationProfileName property in
Communication to
control data transport security characteristics. The
secure property is ignored if there is a
value in the secureCommunicationProfileName
property. If true, use TLS to secure
communication to the host, if false do not.
Optional. Default value is false.
|
|
String | Distribution listener interface address. This address can
be specified as an IPv4 address, IPv6 address, or DNS name. DNS
names can only be used to bind to an IPv4 address. A special
prefix of IPoSDP: indicates that the address
is an Infiniband sockets direct protocol interface (Linux only).
This field is required and cannot have a value of
0.0.0.0 or an empty string
("") if the Node
configuration (see
epadmin-node(1)) containing the
DistributionListenerInterface object is
referenced in ProxyDiscovery configuration
(see ProxyDiscovery),
otherwise optional. Default value is an empty string which will
bind the listener to all interfaces.
|
Example 7. DistributionListenerInterface object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
distributionListenerInterfaces =
[
{
dataTransportPort = 1234
secure = true
address = "myhost.com"
}
{
address = "127.0.0.1"
}
{
address = "IPoSDP:192.168.1.101"
}
{
secure = true
address = "fe80::8a63:dfff:fec3:7abd"
}
]
}
}
}
}
}The metric object defines the metric configuration options.
Metric object properties
Example 8. Metric object snippet
name = "metric-configuration"
version = "1.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A1.X" =
{
description = "my node"
nodeType = "nodetype1"
metric =
{
sampleIdleTimeMinutes = 10
metricUpdateIntervalSeconds = 1
}
}
"A2.X" = { }
}
}
}The Administration object defines the
network communication options for a node's administration connectivity.
Figure 8, “Administration relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Administration object properties and a snippet for these properties is in Example 9, “Administration object snippet”.
Warning
IP addresses specified in the address
configuration property must be quoted. See Example 9, “Administration object snippet”.
Administration object properties
| Name | Type | Description |
|---|---|---|
|
String | Administration listener interface address. This address
can be specified as an IPv4, IPv6, or DNS name. An empty string
("") will listen on all installed interfaces.
If a DNS name is specified, the listener is bound to an IPv6
address if available, otherwise an IPv4 address is used. This
field is required and cannot have a value of
0.0.0.0 or an empty string if the
Node configuration (see
epadmin-node(1)) containing the
Administration object is referenced in
ProxyDiscovery configuration (see ProxyDiscovery), otherwise
optional. Default value is all interfaces on the local
machine.
|
|
long | Administration transport port number. A value of
0 causes the node to auto-generate the port
number. This field is required and cannot have a value of 0 if
the Node configuration (see
epadmin-node(1)) containing the
Administration object is referenced in
ProxyDiscovery configuration (see ProxyDiscovery), otherwise
optional. Default value is 0.
|
|
String [ ] | Disable audit logging for specific URL paths. Multiple partial path values can be specified. All paths starting with the configured values do not generate audit log entries. Optional. No default value. |
|
boolean | Enable administration web server if value is
true. A value of false
disables the administration web server. Optional. Default value
is true.
|
|
An enumeration with valid values of
CACHE_FOREVER,
DO_NOT_CACHE, or
TIMED_CACHE.
|
Controls the caching of downloaded files.
CACHE_FOREVER stores the files forever — they
are never deleted. DO_NOT_CACHE never stores
downloaded files on the node — they are immediately deleted
after use. TIMED_CACHE caches the files for
the amount of time specified in
webMaximumFileCacheTimeMinutes. Optional.
Default value is TIMED_CACHE.
|
|
An enumeration with valid values of
UNLIMITED_FILE_SIZE.
|
Controls the maximum size of downloaded files.
FILE_UPLOAD_NOT_ALLOWED disables file
downloads. LIMITED_FILE_SIZE restricts file
size to the value specified in
UNLIMITED_FILE_SIZE sets no limit on
downloaded file size. Optional. Default value is
LIMITED_FILE_SIZE.
|
|
long | Time in minutes to cache downloaded files if
webFileCacheTimeHandling is set to
TIMED_CACHE. Value must be > 0. Optional.
Default value is 15.
|
|
long | Maximum file size in megabytes for downloaded files if
webFileSizeHandling is set to
LIMITED_FILE_SIZE. Value must be > 0.
Optional. Default value is 5.
|
|
long | Administration web server port number. A value of
0 causes the node to auto-generate the port
number starting from 8008. Optional. Default value is
0.
|
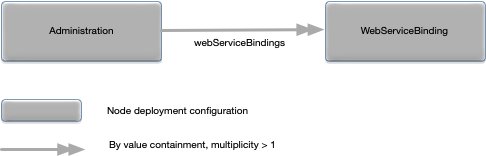
|
Associative array of WebServiceBinding
configuration objects keyed by web service name names.
|
An associative array of
WebServiceBinding (see WebServiceBinding) configuration
objects indexed by web service names. Optional.
|
|
boolean | Enable Web UI for configured web service endpoints if
value is true. A value of
false disables the Web UI. Optional. Default
value is true.
|
Example 9. Administration object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
administration =
{
address = "myhost.com"
transportPort = 1234
webPort = 9876
webEnable = true
webUIEnable = true
webAuditLogDisableUrlPaths = ["prometheus-metrics", "healthcheck"]
webFileCacheTimeHandling = TIMED_CACHE
webMaximumFileCacheTimeMinutes = 5
webFileSizeHandling = LIMITED_FILE_SIZE
webMaximumFileSizeMegabytes = 10
webServiceBindings =
{
"admin" = { ... }
"metrics" = { ... }
}
}
}
}
}
}
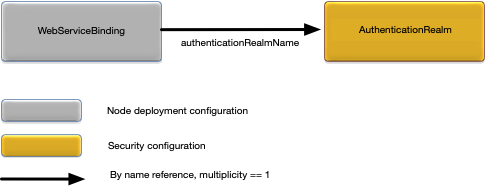
}The WebServiceBinding object defines
the authentication realm associated with a web service. This provides a
mechanism to override the default node administration authentication
realm for a specific web service. Figure 9, “WebServiceBinding relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in WebServiceBinding object properties and a snippet for these properties is in Example 10, “WebServiceBinding object snippet”.
WebServiceBinding object properties
| Name | Type | Description |
|---|---|---|
|
String | Name of an authentication realm (see Secure Communication Server Profile) to use for authentication for this web service. An empty value disables authentication for the web service. Optional. |
Example 10. WebServiceBinding object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
administration =
{
webServiceBindings =
{
"admin" =
{
authenticationRealmName = "my-local-auth-realm"
}
"metrics" =
{
authenticationRealmName = "my-other-local-auth-realm"
}
//
// Disable authentication for healthcheck
//
"healthcheck" = { }
}
}
}
}
}
}
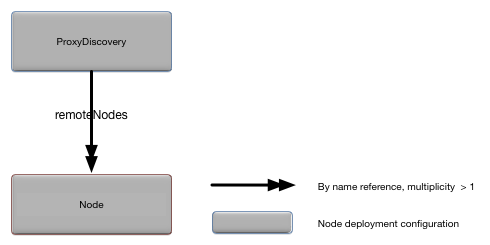
}The ProxyDiscovery object defines the
nodes for which this node is providing proxy discovery services. Figure 10, “ProxyDiscovery relationships” shows the relationships to
other configuration objects.
Additional audits are applied to the remote nodes
specified in the remoteNodes property,
specifically:
-
Administration.transportPortmust be set (see Administration) in the remote node. -
Administration.addressmust be set (see Administration) in the remote node. -
DistributionListenerInterface.dataTransportPortmust be set (see DistributionListenerInterface) in the remote node. -
DistributionListenerInterface.addressmust be set (see DistributionListenerInterface) in the remote node. -
The range of ports defined by the
DistributionListenerInterface.dataTransportPort(see DistributionListenerInterface) and theCommunication.numberSearchPorts(see Communication) cannot overlap for the nodes specified in theremoteNodesproperty.
Any audit failures will cause the node deploy configuration to fail activation.
A detailed description of the configuration object properties is in ProxyDiscovery object properties and a snippet for these properties is in Example 11, “ProxyDiscovery object snippet”.
ProxyDiscovery object properties
| Name | Type | Description |
|---|---|---|
|
String [ ] | List of remote nodes for which to provide proxy discovery
services. All of the specified nodes in this property must be
defined in the NodeDeploy.nodes property (see
NodeDeploy) and be in
the same cluster as the node in which they are contained . See
the Javadoc for java.util.regex.Pattern for
the syntax of the regular expressions that can be used.
Optional. No default.
|
Example 11. ProxyDiscovery object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
//
// Node A.X will provide proxy
// discovery for B.X and C.X
// The data transport and administration
// address and port number must be
// configured for B.X and C.X
// in the same node deploy configuration
// as A.X
//
proxyDiscovery =
{
remoteNodes = ["B.X", "C.X"]
}
}
}
//
// administration and distribution
// listener addresses and ports must be
// configured for node B.X and C.X
// so that they are available
// for node A.X to provide proxy information
//
"B.X" =
{
communication =
{
administration =
{
address = "myhost.com"
transportPort = 1234
}
distributionListenerInterfaces =
[
{
dataTransportPort = 6789
address = "myhost.com"
}
]
}
}
"C.X" =
{
communication =
{
administration =
{
address = "myotherhost.com"
transportPort = 1234
}
distributionListenerInterfaces =
[
{
dataTransportPort = 6789
address = "myotherhost.com"
}
]
}
}
}
}
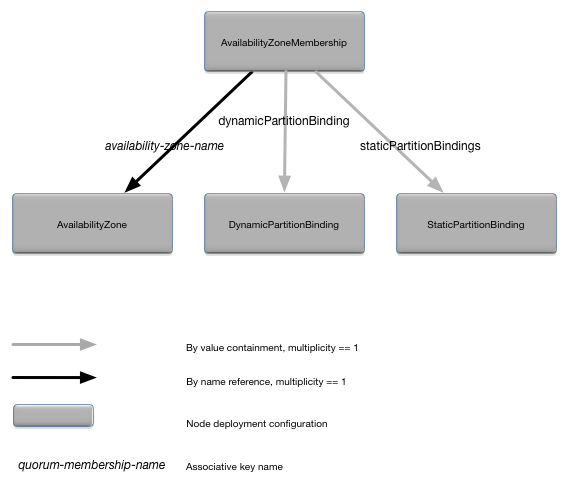
}The AvailabilityZoneMembership object
defines the availability zone membership for a node. Figure 11, “AvailabilityZoneMembership relationships” shows the relationships
to other configuration objects.
A detailed description of the configuration object properties is in AvailabilityZoneMembership object properties and a snippet for these properties is in Example 12, “AvailabilityZoneMembership object snippet”.
AvailabilityZoneMembership object properties
| Name | Type | Description |
|---|---|---|
|
long | Number of quorum votes for this node in the specified availability zone. Optional. Default value is 1. |
|
DynamicPartitionBinding configuration
object.
|
Dynamic partition binding (see DynamicPartitionBinding). This property can only be specified if the associated availability zone is using a dynamic data distribution policy. Optional. No default value. |
|
Associative array of
StaticPartitionBinding objects keyed by
partition names.
|
Static partition binding for the node (see StaticPartitionBinding). This property
can only be specified if the associated availability zone is
using a static data distribution policy. The availability zone
must be defined in
<availability-zone-name>.staticPartitionPolicy.staticPartitions.
Optional. No default.
|
Example 12. AvailabilityZoneMembership object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
availabilityZoneMemberships =
{
"active-active" =
{
votes = 2
staticPartitionBindings = { ... }
}
}
}
}
availabilityZones =
{
"active-active" = { ... }
}
}
}The StaticPartitionBinding object
defines the static partition binding for a node. Figure 12, “StaticPartitionBinding relationships”
shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in StaticPartitionBinding object properties and a snippet for these properties is in Example 13, “StaticPartitionBinding object snippet”.
StaticPartitionBinding object properties
Example 13. StaticPartitionBinding object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
availabilityZoneMemberships =
{
"active-active" =
{
staticPartitionBindings =
{
"P1" =
{
type = "ACTIVE"
replication = "SYNCHRONOUS"
},
"P2" =
{
type = "REPLICA"
replication = "ASYNCHRONOUS"
}
}
}
}
}
}
availabilityZones =
{
"active-active" =
{
dataDistributionPolicy = "static-data-distribution-policy"
staticPartitionPolicy =
{
staticPartitions =
{
"P1" = { },
"P2" = { },
}
}
}
}
}
}The DynamicPartitionBinding object
defines a dynamic partition binding for a node. Dynamic partitions can
also be bound to a node using the
primaryMemberPattern and the
backupMemberPattern properties in the
DynamicPartitionPolicy configuration object (see
DynamicPartitionPolicy). Figure 13, “DynamicPartitionBinding relationships”
shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in DynamicPartitionBinding object properties and a snippet for these properties is in Example 14, “DynamicPartitionBinding object snippet”.
Example 14. DynamicPartitionBinding object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
availabilityZoneMemberships =
{
"elastic-credit" =
{
dynamicPartitionBinding =
{
type = "PRIMARY"
}
}
}
}
}
availabilityZones =
{
"elastic-credit" =
{
dataDistributionPolicy = "dynamic-credit-distribution-policy"
}
}
}
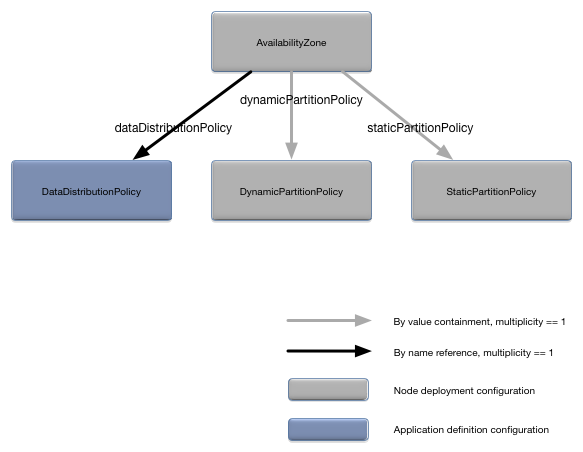
}The AvailabilityZone object defines an
availability zone. There is always a default availability zone defined
even if this configuration object is not specified. See Default Availability Zone for
details. Figure 14, “AvailabilityZone relationships”
shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in AvailabilityZone object properties and a snippet for these properties is in Example 15, “AvailabilityZone object snippet”.
AvailabilityZone object properties
| Name | Type | Description |
|---|---|---|
|
Long | Minimum percentage of node votes to maintain a quorum.
This property is mutually exclusive of the
minimumNumberOfVotes property. If neither
this property or the minimumNumberOfVotes
property is set, quorums are disabled. Optional. No default
value.
|
|
Long | Minimum number nodes to maintain a quorum. This property
is mutually exclusive of the
percentageOfVotes property. If neither this
property or the percentageOfVotes property is
set, quorums are disabled. Optional. No default value.
|
|
String | The data distribution policy for this availability zone, as defined in the application definition configuration. Optional. No default value. |
|
DynamicPartitionPolicy configuration
object.
|
Dynamic partition policy configuration (see DynamicPartitionPolicy). A dynamic data
distribution policy must be specified in the
dataDistributionPolicy property if this
property is set. Optional. No default value.
|
|
StaticPartitionPolicy configuration
object.
|
Static partition policy configuration (see StaticPartitionBinding). A static data
distribution policy must be specified in the
dataDistributionPolicy property if this
property is set. Optional. No default value.
|
|
String | A regular expression describing which nodes are part of a
quorum. All nodes matching this regular expression are part of
the quorum. Such members get a single quorum vote. Quorum
membership can be expressed in one or both of two ways: via this
regular expression or explicitly by each node. See the Javadoc
for java.util.regex.Pattern for the syntax of
the regular expressions that can be used. Optional. No default
value.
|
Example 15. AvailabilityZone object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
availabilityZones =
{
"active-active" =
{
dataDistributionPolicy = "static-data-distribution-policy"
staticPartitionPolicy = { ... }
}
"elastic-dr" =
{
dataDistributionPolicy = "dynamic-data-distribution-policy"
dynamicPartitionPolicy = { ... }
}
"west-coast-quorum" =
{
minimiumNumberOfVotes = 2
quorumMemberPattern = ".*\\.west\\.X"
}
}
}
}The DynamicPartitionPolicy object
defines a dynamic partition policy for an availability zone. Figure 15, “DynamicPartitionPolicy relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in DynamicPartitionPolicy object properties and a snippet for these properties is in Example 16, “DynamicPartitionPolicy object snippet”.
DynamicPartitionPolicy object properties
| Name | Type | Description |
|---|---|---|
|
String | A regular expression describing the primary node
membership for this dynamic partition policy. Membership can be
expressed in one, or both, of two ways: via this regular
expression or explicitly for each node (see DynamicPartitionBinding). The bindings
are additive. See the Javadoc for
java.util.regex.Pattern for the syntax of the
regular expressions that can be used. Optional. Default value is
all nodes in a cluster, unless
backupMemberPattern is specified, in which
case, there is no default value. A regular expression that does
not match any nodes in the cluster must be specified to disable
this binding if backupMemberPattern is not
specified.
|
|
String | A regular expression describing the backup node
membership for this dynamic partition policy. Membership can be
expressed in one, or both, of two ways: via this regular
expression or explicitly for each node (see DynamicPartitionBinding). The bindings
are additive. If backup nodes are defined, all primary nodes
must be explicitly defined; that is, setting this property
disables the primaryMemberPattern default
value. See the Javadoc for
java.util.regex.Pattern for the syntax of the
regular expressions that can be used. Optional. No
default.
|
Example 16. DynamicPartitionPolicy object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
availabilityZones =
{
"elastic-dr" =
{
dataDistributionPolicy = "dynamic-data-distribution-policy"
dynamicPartitionPolicy =
{
primaryMemberPattern = ".*\\.west\\.X"
backupMemberPattern = ".*\\.east\\.X"
}
}
}
}
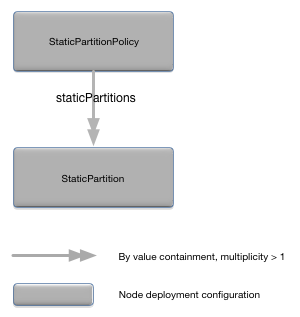
}The StaticPartitionPolicy object
defines a static partition policy for an availability zone. Figure 16, “StaticPartitionPolicy relationships” shows the relationships
to other configuration objects.
A detailed description of the configuration object properties is in StaticPartitionPolicy object properties and a snippet for these properties is in Example 17, “StaticPartitionPolicy object snippet”.
StaticPartitionPolicy object properties
| Name | Type | Description |
|---|---|---|
|
Enumeration. Valid values are
REVERSE_CONFIGURATION and
REVERSE_LOCAL_THEN_REMOTE.
|
REVERSE_CONFIGURATION disables the
partitions in reverse order based on the order they appear in
the configuration file.
REVERSE_LOCAL_THEN_REMOTE disables all
partitions that have the local node as the active node, then
disable all partitions where a remote node is the active node.
Optional. Default value is
REVERSE_CONFIGURATION.
|
|
Enumeration. Valid values are
CONFIGURATION and
REMOTE_THEN_LOCAL.
|
CONFIGURATION enables the partitions
based on the order they appear in the configuration file.
REMOTE_THEN_LOCAL enables all partitions that
have a remote node as the active node, then enables the
partitions where the active node is the local node. Optional.
Default value is CONFIGURATION.
|
staticPartitions |
Associative array of StaticPartition
objects keyed by partition name.
|
StaticPartition configuration objects.
Optional. No default.
|
|
String | A regular expression describing which nodes know about
the partitions in this static partition policy. These nodes may
or may not be hosting the partitions defined in the static
partition policy. The complete set of nodes that know about
these partitions is defined by this regular expression and
explicit node binding (see StaticPartitionBinding). See the
Javadoc for java.util.regex.Pattern
for the syntax of the regular expressions that can be used.
Optional. Default value is the explicit partition binding in the
containing availability zone.
|
Example 17. StaticPartitionPolicy object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
availabilityZones =
{
"active-active" =
{
dataDistributionPolicy = "static-data-distribution-policy"
staticPartitionPolicy =
{
enableOrder = "CONFIGURATION"
disableOrder = "REVERSE_CONFIGURATION"
loadOnNodesPattern = ".*\\.east\\.X"
staticPartitions =
{
"P1" = { },
"P2" = { },
}
}
}
}
}
}The StaticPartition object defines a
static partition. Figure 17, “StaticPartition relationships” shows
the relationships to other configuration objects.
A detailed description of the configuration object properties is in StaticPartition object properties and a snippet for these properties is in Example 18, “StaticPartition object snippet”.
StaticPartition object properties
Example 18. StaticPartition object snippet
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
availabilityZones =
{
"active-active" =
{
dataDistributionPolicy = "static-data-distribution-policy"
staticPartitionPolicy =
{
staticPartitions =
{
"P1" =
{
rank = 2
},
"P2" =
{
rank = 1
}
}
}
}
}
}
}